“breach”
- An act of breaking or failing to observe a law, agreement, or code of conduct.
- A break in relations.
- A gap in a wall, barrier, or defence, especially one made by an attacking army
- The Rising Tide of Data Breaches in South Africa
- Data Privacy and Data Governance
- How must companies deal with a data breach in terms of South Africa’s Protection of Personal Information Act (PoPIA)?
- Data Governance is a necessity
- Choosing a tool to manage data privacy and PoPIA compliance
- Act Now or Pay Later

The Rising Tide of Data Breaches in South Africa
South Africa’s cybersecurity landscape is under siege. The Information Regulator reported a staggering threefold increase in data breaches, soaring from 500 incidents in 2022 to over 1,700 in 2023.
With breaches costing businesses between R18 million to R360 million per incident—and averaging R53 million—the urgency for compliance has never been greater.
Worse, organizations take 227 days on average to identify and contain breaches, lagging behind the global average.
Human error drives 95% of breaches, while insider threats and ransomware attacks compound the crisis. For small businesses, the stakes are existential: 60% may shutter within six months of a major breach.
Ironically, while we posted in 2017 that the regulatory need to protect sensitive data is a key driver for data governance, data incidents continue to increase both in volume and impact year on year.
Understanding the Implications of Data Breaches
A breach isn’t just a technical failure—it’s a legal, financial, and reputational catastrophe. Under South Africa’s Protection of Personal Information Act (PoPIA), companies face fines, lawsuits, and even 15-year prison sentences for non-compliance. The 2023 leak of 30 million South Africans’ data exposed vulnerabilities, highlighting risks like identity theft and fraud. Globally, regulations like the EU’s GDPR demand breach reporting within 72 hours, affecting SA firms operating internationally.
Data Privacy and Data Governance
Protection of Personal Information Act
The Protection of Personal Information Act (PoPIA) was promulgated in 2013 and requires companies to take adequate precautions against data loss. The PoPI Act defines a breach as having occurred when there are reasonable grounds to believe that personal information of a data subject has been accessed or acquired by any unauthorized person. This means that both intentional and unintentional incidents can constitute a data breach under POPIA. Once a breach has been identified, the responsible party must take comprehensive, mandatory data breach reporting obligations and notify the Information Regulator as soon as reasonably possible. The breach notification must include the following details:
– A description of the breach and the type of information involved
– The identity of the data subject or group of data subjects affected by the breach
– The identity of any third party or parties to whom the personal information was disclosed
– The steps taken or proposed to be taken to address the breach
The Act allows plaintiffs to seek damages for compensation for losses suffered as the result of a breach, along with aggravated damages and interest.
Global Data Protection Regulations
In Europe, the Global Data Protection Regulations (GDPR) are similar regulations affecting business holding data related to EU citizens. Many larger South African firms are directly affected, as they do business with, and in EU countries. GDPR requires that breaches must be reported within 72 hours to allow the injured party to take precautions.
We should also remember that many other African countries have their own similar laws. Companies doing business in the rest of Africa should understand the implications of managing data that may shift from jurisdiction to jurisdiction, and ensure that adequate governance in is in place to ensure compliance.
How must companies deal with a data breach in terms of South Africa’s Protection of Personal Information Act (PoPIA)?
In South Africa, the Protection of Personal Information Act (POPIA) requires all organizations to take appropriate, reasonable technical and organizational measures to secure the integrity and confidentiality of personal information in their possession or control. This includes preventing unlawful access to or processing of personal information. In case of a data breach, companies must comply with the notification requirements contained in section 22 of POPIA. Here are the steps that companies must take to deal with a data breach in terms of South Africa’s POPIA:
1. Identify the breach: Companies must identify the nature and extent of the breach, including the type of personal information involved, the number of individuals affected, and the potential harm that may result. This will typically require an assessment of the systems and processes that may have been compromised, which can be particularly difficult in large, connected enterprises.
2. Contain the breach: Companies must take immediate action to contain the breach and prevent further unauthorized access or disclosure of personal information. This may include shutting down affected systems or implementing data security measures.
3. Evaluate the risks: Companies must assess the risks associated with the breach, including the likelihood of harm to affected individuals, and determine the appropriate course of action. This requires an understanding of both the data that has been compromised and the potential impact to the data subjects.
4. Notify the regulator: Companies must report the breach to the Information Regulator as soon as reasonably possible after becoming aware of the breach. The notification must include all relevant information about the breach, including the steps taken to contain it. An automated audit trail of the steps taken and decisions made to contain the breach will simplify this.
5. Notify affected individuals: Companies must notify affected individuals of the breach, unless the identity of the individuals cannot be established. The notification must include all relevant information about the breach, the potential harm that may result, and the steps that affected individuals can take to protect themselves.
6. Implement remedial measures: Companies must take appropriate remedial measures to address the breach, including providing affected individuals with access to credit monitoring services or other forms of identity theft protection.
7. Review and update policies and procedures: Companies must review and update their policies and procedures to prevent future breaches and ensure compliance with POPIA. Again, an automated audit trail will make it easier both to track what actions have been taken and to keep a history of improvements over time.
A tool, or tools, that support the above steps is essential to any but the smallest organisations.
Failure to comply has consequences
Non-compliance with POPIA can result in massive fines and lengthy prison sentences of up to 15 years. Companies may also face the risk of class action lawsuits under POPIA, and severe reputational damage for non-compliance. Would you continue to do business with a company that lost or sold your personal identifiers or contact details to unknown third parties?
Therefore, it is important for companies to take POPIA seriously, and implement appropriate measures to protect personal information and respond to data breaches
Data Governance is a necessity
GDPR and PoPIA signal a shift in how we think about data privacy. These acts move the focus away from the data – those bits and pieces of information typically flagged for privacy – to focus instead on the fundamental rights of the data subjects.
PoPIA shifts focus from mere data protection to accountability and ethical use. Effective governance requires:
- Collaboration: Cross-functional input from compliance officers, IT, and process owners.
- Visibility: Tools to monitor data flows and flag anomalies (e.g., AI-driven tagging of sensitive data).
- Lifecycle Management: Map PoPIA principles (like Purpose Specification and Security Safeguards) to every data stage.
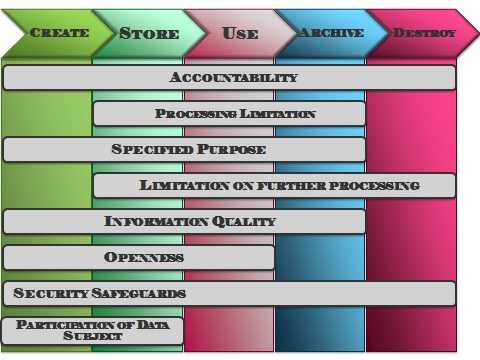
PoPIA requires that organisations put processes in place to ensure that data is only used for the purpose for which it was intended, that data is protected from unauthorized access, and that there is accountability for how data is used within the business.
At its core, PoPIA requires the implementation of an organization-wide data governance program, reliant upon both collaboration and shared accountability. The structure of governance programs can widely vary, but when viewed from a single-process perspective, compliance requires several considerations and contributions from many different competency areas. Chief among these is the process owner, who must define the processing principles. Supporting competencies include application owners, vendor management, compliance officers, etc.—all of whom must provide input and approvals for varying regulatory provisions. The challenge of achieving compliance on an initial and ongoing basis is a multi-faceted and shared undertaking, further complicated by the organizations’ limited visibility and data monitoring capabilities.
The operating principles of PoPIA
The key principals of PoPIA are summarized below and linked to their applicability at different stages of the data life cycle.
Accountability
- Responsible party to ensure conditions for lawful processing
- Processing Limitation
- Lawfulness of processing
Processing Limitations
- Consent, justification and objection
- Collection directly from data subject
Purpose Specification
- Collection for specific purpose
- Retention and restriction of records
Further Processing Limitation
- Further processing to be compatible with purpose of collection
Information Quality
- Quality of information
Openness
- Documentation
- Notification to data subject when collecting personal information
Security Safeguards
- Security measures on integrity and confidentiality of personal information
- Information processed by operator or person acting under authority
- Security measures regarding information processed by operator
- Notification of security compromises
Data Subject Participation
- Access to personal information
- Correction of personal information
- Manner of access
Choosing a tool to manage data privacy and PoPIA compliance
The complexity of enterprise data landscapes means that a breach cannot be managed without tools. Typically, the choice that has to be made is between a specialist data privacy policy manager and a multi-use data governance platform. Both can be useful tools for managing data privacy in an organization. However, they have different strengths and weaknesses, which should be considered when deciding which one to use.
Pros of a specialist data privacy policy manager:
- Expertise: A specialist data privacy policy manager has deep knowledge and expertise in data privacy regulations and can help ensure that your organization’s policies are in compliance with current laws and regulations.
- Focus: A specialist data privacy policy manager’s primary focus is on data privacy, which means they are more likely to be up to date on the latest privacy regulations and trends.
- Customization: A specialist data privacy policy manager can customize policies to meet the specific needs of an organization, which can ensure that policies are tailored to fit the organization’s unique situation.
Cons of a specialist data privacy policy manager:
- Cost: A specialist data privacy policy manager can be expensive, especially for small organizations with limited budgets.
- Limited scope: A specialist data privacy policy manager’s scope is limited to data privacy policies and may not cover all aspects of data governance, particularly with respect to tracking the use of data across the organisation
- Limited scalability: May not scale to meet the needs of a large enterprise
Pros of a data governance platform:
- Comprehensive: A data governance platform provides a comprehensive approach to data governance, which means that it can cover all aspects of data management, including data privacy.
- Scalability: A data governance platform can be scaled to meet the needs of an organization as it grows, which can be beneficial for organizations that are expanding.
- Integration: A data governance platform can be integrated with other systems and tools, which can help streamline data management processes.
Cons of a data governance platform:
- Complexity: A data governance platform can be complex and difficult to set up, which may require additional training or expertise.
- Cost: A data governance platform can be expensive, especially for small organizations with limited budgets. However, the multipurpose nature of these tools may allow the cost to be split across additional functions such as enablnig analytics.
- Overwhelming: A data governance platform can provide a large amount of data and information, which can be overwhelming for some users.
In summary, both a specialist data privacy policy manager and a data governance platform have their pros and cons. Organizations should consider their specific needs and budget when deciding which tool to use to manage data privacy. A specialist data privacy policy manager may be more appropriate for smaller organizations that require focused expertise, while a data governance platform may be more suitable for larger organizations with more complex data management needs.
Precisely Data360 for addressing Data Privacy Compliance
Precisely Data360 is a collaborative Data Governance solution that provides our clients a platform to gain a broad and comprehensive understanding of their enterprise data. Some features of Data 360 include:
- Intuitive business focused GUI
- Link activities to business goals and objectives (such as specific aspects of PoPIA) with our top-down, Information Value Management approach.
- Comprehensive dash boarding and metrics to track and manage governance activities and impact on business
- Impact analysis and tracking with comprehensive lineage and other visual tools
- Assign responsibilities at a granular level, from individual attributes to data models, report, or systems.
- Easy configuration and extension to meet any need
- Set up comprehensive workflows (such as breach management processes) with easy integration into other tools
- AI driven tagging of sensitive data
- Can include our PoPIA accelerator, a predefined set of policies and artifacts to accelerate PoPIA compliance

Download the datasheet, or get in touch for more information.
Act Now or Pay Later
With ransomware targeting Africa and 1 in 10 breaches caused by internal staff, complacency is a luxury businesses can’t afford. Precisely Data360’s PoPIA Accelerator predefines policies, slashing compliance timelines.
Conclusion
The surge in breaches isn’t just a trend—it’s a wake-up call. Invest in governance, leverage scalable tools, and foster a culture of accountability. As PoPIA enforcers ramp up scrutiny, proactive compliance isn’t optional—it’s survival.

Leave a comment