According to Gartner, by 2023, 75% of security failures will result from inadequate management of identities, access, and privileges. In other words, the bulk will come from the abuse of access assigned to authorised users.
Traditional IAM approaches and security controls are not designed to solve the problem.
What are some of the challenges, and how do we overcome them?

Multi/Hybrid-cloud
While most organisations are shifting some processing capabilities to the cloud, substantial capabilities remain on-premise.
For example, I may retain my existing enterprise data warehouse on-premise, while creating a data lake in the cloud. In many cases, organisations have not standardised on a single cloud provider – running some capabilities on Azure, for example, and others on AWS.
Sensitive data may coexist therefore across multiple platforms in multiple environments including:
- On-premise databases and data warehouses
- Amazon EMR
- Snowflake
- Azure
This creates substantial complexity from an access management perspective, as each platform and environment brings its own approach and nuances, making it difficult to apply consistent policies and requiring substantial duplication of effort. Some of these platforms are highly technical, making it difficult for non-technical data stewards to apply or understand access policies that have been applied.
A single, unified, data authorisation platform, like Okera, that allows policies to be defined once, and applied consistently across the entire data landscape reduces this complexity, cuts out repetition of labour, and ensures that data privacy leaders and auditors can understand and measure compliance with policies that have been defined.
Coarse-grained access
Another practical reality is that traditional role-based access management systems do not offer sufficiently fine-grained access control to support modern data privacy requirements.
Sensitive data is not typically constrained to a single table or view. Instead, it lies across every schema and within almost every table.
Access policies and controls need to be sufficiently nuanced to deal with the complexities of regulation like PoPIA which expects minimum levels of access and applies nuanced rules themselves.
For example, PoPIA pays special attention to the data of children. This means that I may need to limit access to specific records within my data, based on an age calculation, as well as to specific fields within my data (such as name), depending on my user’s role and permissions.
We need the ability to set up complex policies, that can cope with these nuances, and that do so with transparency i.e. it must be easy to understand which policies are applied.
All or nothing
Even within these constraints, an all-or-nothing approach may not be useful. Let’s assume, for example, that a BI developer should not have access to customer names.
If they need to create a report on, for example, Sales per customer, they will need access to customer information. A platform that can anonymise data but leave it available for analytics solves this problem.
Provide visibility into data usage
Many data lake owners struggle to understand the usage of the lake, while the data privacy team needs to know their sensitive data exposure.
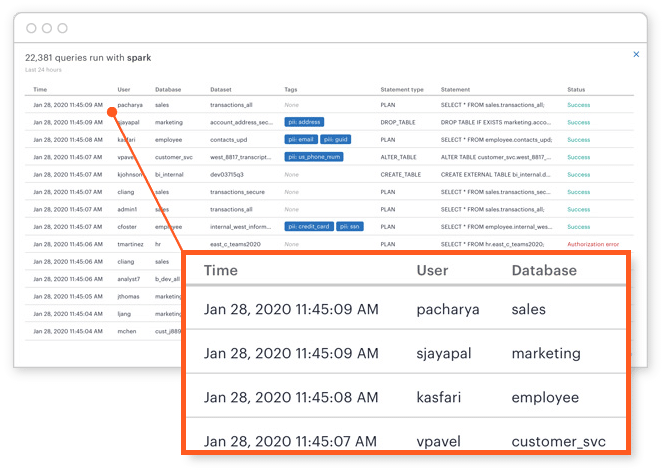
Okera Spotlight helps solve both of these problems by automatically discovering sensitive data and capturing all activity in real-time across all analytics tools. It provides critical metrics, like top users and applications for live, holistic insight into who is accessing what data in your data lake.
Data stewards can drill down into the detail to identify suspect access patterns, or even trigger alerts caused by unusual behaviour.
Stop abusive access
The combination of capabilities offered through Okera goes a long way to addressing the access management risks identified by Gartner.
Assuming that a hacker successfully phishes a password for a BI developer – they will only have access to a subset of data, potentially anonymised, according to that developer’s profile. If they should try to do something unusual, such as download the data, this unusual behaviour can trigger an alert for immediate action.
Give us a call to discuss your data privacy challenges
Gartner, Best Practices for Optimizing IGA Access Certification, Gautham Mudra, 4 April 2022

Leave a comment